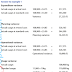
In Redis Server, the command to retrieve key-value differs by data type.
Here are the commands to retrieve the key value:
if the value is of type string,
GET <key>
if the value is of type hash,
HGETALL <key>
if the value is of type lists,
lrange <key> <start> <end>
if the value is of type sets,
smembers <key>
if the value is of type sorted sets,
ZRANGEBYSCORE <key> <min> <max>
The command to check the type of value a key mapping to:
type <key>
Source:
https://www.attackdefense.com/
https://stackoverflow.com/questions/37953019/wrongtype-operation-against-a-key-holding-the-wrong-kind-of-value-php
22 January 2020
20 January 2020
MySQL Network Recon - Exercise No. 2
The command used to connect to a remote MySQL database.
MySQL [(none)]> show databases;
MySQL [data]> show tables;
root@% = allows connection from user 'root' from any host, local or TCP (internet).
root@localhost = only allows connection from 'root' on the machine running the MySQL server.
MySQL [information_schema]> select * from user_privileges where GRANTEE like '%\%%' ;
Sources : https://www.attackdefense.com/
MySQL [(none)]> show databases;
MySQL [data]> show tables;
root@% = allows connection from user 'root' from any host, local or TCP (internet).
root@localhost = only allows connection from 'root' on the machine running the MySQL server.
MySQL [information_schema]> select * from user_privileges where GRANTEE like '%\%%' ;
Sources : https://www.attackdefense.com/
19 January 2020
ACCA PM Chapter 7 - PRICING - Introduction, Cost plus pricing
Factors influencing selling price:
Cost-plus pricing
1. Full cost plus - Full cost includes a shared overhead and also often includes non-production costs.
Advantages:
Disadvantages:
2. Marginal cost plus - the marginal (or incremental) cost of producing a unit and adding a mark-up.
Advantages:
Disadvantages:
3. Opportunity cost plus - a marginal cost approach but also includes within the cost any opportunities foregone. It is a relevant costing approach.
Source: https://opentuition.com/acca/pm/acca-performance-management-pm-lectures/
- costs
- competitors
- customers
Cost-plus pricing
1. Full cost plus - Full cost includes a shared overhead and also often includes non-production costs.
Advantages:
- Easy
- Standard Policy
- "Guaranties" Profit
Disadvantages:
- Ignores Competition
- Ignores Effect of Price on Demand
- Absorption of Fixed Overheads
2. Marginal cost plus - the marginal (or incremental) cost of producing a unit and adding a mark-up.
Advantages:
- Easy
- Standard Policy
- No need to absorb Fixed Overheads
Disadvantages:
- Ignores Competition
- Ignores Effect of Price on Demand
- What % to add to make sure Fixed Overheads covered?
3. Opportunity cost plus - a marginal cost approach but also includes within the cost any opportunities foregone. It is a relevant costing approach.
Source: https://opentuition.com/acca/pm/acca-performance-management-pm-lectures/
18 January 2020
LAN Technologies - MAC Address Table and Gratuitous ARP
Classification of MAC Address Entries
Classification of secure MAC address
- Dynamic MAC address entries
- Static MAC address entries
- Blackhole MAC address entries
Classification of secure MAC address
- Secure dynamic MAC address
- Secure static MAC address
- Sticky MAC address
Configuring MAC Address Anti-flapping
- Increases the MAC address learning priority of an interface.
- Prohibits MAC address entry overriding between interfaces with the same priority.
Gratuitous ARP functions:
- Checks for IP address conflicts
- Advertises a new MAC address
- Notifies other devices of master/backup switchover in a Virtual Router Redundancy Protocol (VRRP) group
Source: https://ilearningx.huawei.com/
MEMCACHED Network Recon - Exercise No. 1
The number of key-value pairs stored on the Memcached server.
- memcstat --servers=<ip address> | grep curr_items
The value stored in the key “password” on the Memcached server.
- memccat --servers=<ip address> password
Using memcached-tool,
- /usr/share/memcached/scripts/memcached-tool <ip address:port number> dump
Using msfconsole - memcached_extractor,
Segmented LRU,
Using Least Recently Used (LRU) crawler to output every valid item,
- lru_crawler metadump all
Sources :
15 January 2020
ACCA PM Chapter 6 - Limiting Factors
Linear Programming
- Define the unknowns in terms of symbols
- Formulate equations for the constraints
- Formulate an equation for the objective
- Graph the constraints and the objective
- Find the optimum solution
Spare capacity
If the optimum solution results in using less than the maximum available of a particular resource, then we have spare capacity of that resource or slack.
Shadow prices (dual price)
Shadow Price is the most EXTRA we would be prepared to pay for an extra unit of the limited resource.
Explicitly Query a DNS record from a specific NameServer
Explicitly Query a DNS record from a specific NameServer:
rober:~$ dig +nottlid +noall +answer @8.8.8.8 boonkeat.com ANY
rober:~$ dig +nottlid +noall +answer @8.8.8.8 boonkeat.com ANY
13 January 2020
ACCA PM Chapter 5 - Key Factor Analysis VS Throughput Accounting
Key Factor Analysis
Contribution = Selling Price - Variable Costs.
Contribution = Profit before Fixed Costs.
Contribution per hour = Contribution / hour
Fixed Costs,
(Assume that original costings were done before knowing about the limit on hours - produce to equal demand)
Contribution - Fixed Costs = Maximum Profit.
Throughput Accounting
Assume the ONLY Variable Cost is Materials.
(ALL Other Costs fixed in total).
Throughput = Revenue - Material Cost.
Return per factory hour = Throughput per hour.
Fixed Costs,
(All Costs other than Materials).
Throughput - Fixed Costs = Maximum Profit.
Total factory costs = all production costs except materials
Cost per factory hour = Total factory costs / Available hours
Throughput Accounting Ratio = Return per factory hour / Cost per factory hour.
Bottleneck
The rate of production will be restricted by the slowest of the machines, and this machine is known as the bottleneck resource.
Source: https://opentuition.com/acca/pm/acca-performance-management-pm-lectures/
Contribution = Selling Price - Variable Costs.
Contribution = Profit before Fixed Costs.
Contribution per hour = Contribution / hour
Fixed Costs,
(Assume that original costings were done before knowing about the limit on hours - produce to equal demand)
Contribution - Fixed Costs = Maximum Profit.
Throughput Accounting
Assume the ONLY Variable Cost is Materials.
(ALL Other Costs fixed in total).
Throughput = Revenue - Material Cost.
Return per factory hour = Throughput per hour.
Fixed Costs,
(All Costs other than Materials).
Throughput - Fixed Costs = Maximum Profit.
Total factory costs = all production costs except materials
Cost per factory hour = Total factory costs / Available hours
Throughput Accounting Ratio = Return per factory hour / Cost per factory hour.
Bottleneck
The rate of production will be restricted by the slowest of the machines, and this machine is known as the bottleneck resource.
Source: https://opentuition.com/acca/pm/acca-performance-management-pm-lectures/
12 January 2020
Domain 1: Security and Risk Management
1.1 Understand and apply concepts of confidentiality, integrity, and availability
1.4 Understand legal and regulatory issues that pertain to information security in a global context
1.5 Understand, adhere to, and promote professional ethics
1.6 Develop, document, and implement security policy, standards, procedures, and guidelines
1.7 Identify, analyze, and prioritize Business Continuity (BC) requirements
1.8 Contribute to and enforce personnel security policies and procedures
1.9 Understand and apply risk management concepts
1.10 Understand and apply threat modeling concepts and methodologies
1.11 Apply risk-based management concepts to the supply chain
1.12 Establish and maintain a security awareness, education, and training program
Source: https://www.udemy.com/course/cissp-domain-1-2/
1.2 Evaluate and apply security governance principles
- Alignment of security function to business strategy, goals, mission, and objectives
- Organizational processes (e.g., acquisitions, divestitures, governance committees)
- Organizational Roles and responsibilities
- Security control frameworks
- Due care/due diligence
1.3 Determine compliance requirements
- Contractual, legal, industry standards, and regulatory requirements
- Privacy requirements
- Cybercrimes and data breaches
- Licensing and intellectual property requirements
- Import/export controls
- Trans-border data flow
- Privacy
1.5 Understand, adhere to, and promote professional ethics
- (ISC)² Code of Professional Ethics
- Organizational code of ethics
1.6 Develop, document, and implement security policy, standards, procedures, and guidelines
1.7 Identify, analyze, and prioritize Business Continuity (BC) requirements
- Develop and document scope and plan
- Business Impact Analysis (BIA)
1.8 Contribute to and enforce personnel security policies and procedures
- Candidate screening and hiring
- Employment agreements and policies
- Onboarding and termination processes
- Vendor, consultant, and contractor agreements
- and controls
- Compliance policy requirements
- Privacy policy requirements
1.9 Understand and apply risk management concepts
- Identify threats and vulnerabilities
- Risk assessment/analysis
- Risk response
- Countermeasure selection and implementation
- Applicable types of controls (e.g., preventive, detective, corrective)
- Security Control Assessment (SCA)
- Monitoring and measurement
- Asset valuation
- Reporting
- Continuous improvement
- Risk frameworks
1.10 Understand and apply threat modeling concepts and methodologies
- Threat modeling methodologies
- Threat modeling concepts
1.11 Apply risk-based management concepts to the supply chain
- Risks associated with hardware, software, and
- services
- Third-party assessment and monitoring
- Minimum security requirements
- Service-level requirements
1.12 Establish and maintain a security awareness, education, and training program
- Methods and techniques to present awareness and training
- Periodic content reviews
- Program effectiveness evaluation
11 January 2020
ACCA PM Chapter 4 - Environmental Management Accounting
1. The focus is to on the efficient use of resources and the disposal of waste and effluent.
2. Three ways of impact in environmental costs.
2. Three ways of impact in environmental costs.
- Cost on excessive resources and cleaning-up.
- Reputation pf the company.
- Fines and penalties.
3. Typical environmental cost, other than waste.
- Raw Materials: Use recyclable material to save costs.
- Transport Costs: Find alternatives.
- Water and Energy consumption: Identify inefficiencies and wasteful practice to save costs.
4. The Accounting method for environmental costs.
- Inflow / Outflow analysis
- All waste in Raw materials as well as energy and water.
- Flow Cost Accounting
- Material (Not Raw)
- System
- Delivery and disposal
- Lifecycle costing
- Design-out the cost before the product launched.
- Environmental Activity-Based Costing
- Environment-related cost (E.g., Sewage plant)
09 January 2020
OSQUERY - Exercise No. 1
“consider JOINing against the users table”
osquery> select * from shell_history WHERE shell_history.uid IN (SELECT uid from users);
Who has stored the SSH private keys on the machine?
osquery> select * from shell_history WHERE shell_history.uid IN (SELECT uid from users) and shell_history.command like '%rsa%';
The path of the ftp service daemon running.
osquery> select path from processes where name='vsftpd';
The complete path of a specific binary run as root.
osquery> select * from shell_history WHERE shell_history.uid IN (SELECT uid from users) and shell_history.command like '%sudo%';
Sources:
https://www.attackdefense.com
https://www.first.org/resources/papers/conf2018/Wilson-Doug_FIRST_20180629.pdf
osquery> select * from shell_history WHERE shell_history.uid IN (SELECT uid from users);
Who has stored the SSH private keys on the machine?
osquery> select * from shell_history WHERE shell_history.uid IN (SELECT uid from users) and shell_history.command like '%rsa%';
The path of the ftp service daemon running.
osquery> select path from processes where name='vsftpd';
The complete path of a specific binary run as root.
osquery> select * from shell_history WHERE shell_history.uid IN (SELECT uid from users) and shell_history.command like '%sudo%';
Sources:
https://www.attackdefense.com
https://www.first.org/resources/papers/conf2018/Wilson-Doug_FIRST_20180629.pdf
08 January 2020
07 January 2020
ACCA PM Chapter 2 - Target Costing
Target Cost is the maximum cost per unit in order to achieve the required profit.
It is used to compare the estimated actual cost. The excess of the actual cost over the target is called "Target Cost Gap".
Possible ways of attempting to close the target cost gap:
The five major characteristics that distinguish services from manufacturing are:
It is used to compare the estimated actual cost. The excess of the actual cost over the target is called "Target Cost Gap".
Possible ways of attempting to close the target cost gap:
- Examine costs to look for cheaper.
- Reexamine design of the product, can we reduce cost without needing to reduce the price.
The five major characteristics that distinguish services from manufacturing are:
- Intangibility
- Inseparability / Simultaneity
- Variability / heterogeneity
- Perishability
- No transfer of ownership
05 January 2020
OSQUERY - Networking Tables
How many network interfaces are present on the machine?
osquery> select * from interface_addresses;
How many DNS servers are configured on the machine?
osquery> select * from dns_resolvers;
208.67.222.222 belongs to OpenDNS.
Which interface is acting as the default gateway for the machine?
osquery> select * from routes;
How many entries are there in the ARP cache?
osquery> select * from arp_cache;
What is the given hostname of the machine?
osquery> select * from etc_hosts;
Source:https://www.attackdefense.com/challengedetails?cid=1044
osquery> select * from interface_addresses;
How many DNS servers are configured on the machine?
osquery> select * from dns_resolvers;
208.67.222.222 belongs to OpenDNS.
Which interface is acting as the default gateway for the machine?
osquery> select * from routes;
How many entries are there in the ARP cache?
osquery> select * from arp_cache;
What is the given hostname of the machine?
osquery> select * from etc_hosts;
Source:https://www.attackdefense.com/challengedetails?cid=1044
04 January 2020
ACCA PM Chapter 1 - Activity Based Costing
Overheads = Expenses
In ACCA F2, we probably used only one cost driver (e.g., labor hours) to calculate costs.
Activity-Based Costing (ABC) attempts to absorb overheads in a more accurate (and therefore more useful) way.
The steps to be followed are as follows:
In ACCA F2, we probably used only one cost driver (e.g., labor hours) to calculate costs.
Activity-Based Costing (ABC) attempts to absorb overheads in a more accurate (and therefore more useful) way.
The steps to be followed are as follows:
- identify the major activities that give rise to overheads (e.g., machining; dispatching of orders)
- determine what causes the cost of each activity – the cost driver (e.g., machine hours; the number of dispatch orders)
- calculate the total cost for each activity – the cost pool (e.g., total machining costs; total costs of despatch department)
- calculate an absorption rate for each cost driver
- calculate the total overhead cost for each product manufactured
- calculate the overhead cost per unit for each product
02 January 2020
Windows PowerShell Basics and Cmdlets
Commands tried:
cd \
dir
ls
ps
Get Help:
PS C:\> Get-Help
PS C:\> Get-Help *process
PS C:\> Get-Help *alias*
Download and install Help files on your computer:
PS C:\> Update-Help
List all alias you can use:
PS C:\> Get-Alias
Get Help for conceptual topics:
PS C:\> Get-Help Get-Help -Examples | more
Get Help for conceptual topics about alias:
PS C:\> Get-Help about_alias | more
Get Help about Get-Command
PS C:\> Get-Help Get-Command | more
Get all the commands:
PS C:\> Get-Command | more
Get all the commands (cmdlet only)
PS C:\> Get-Command -CommandType cmdlet | more
Get detailed Help about Get-Command:
PS C:\> Get-Help Get-Command -full | more
Get detailed Help about Get-Command (Parameter only):
PS C:\> Get-Help Get-Command -Parameter * | more
Get cmdlet with Name containing process:
PS C:\> Get-Command -CommandType cmdlet -Name *process*
Get cmdlet with Name containing service:
PS C:\> Get-Command -CommandType cmdlet -Name *service*
Measure Object (cmdlet only):
PS C:\> Get-Command -CommandType cmdlet | Measure-Object
Get all Processes:
PS C:\> Get-Process | more
Get all Services:
PS C:\> Get-Service | more
Get Commands with stop as a verb:
PS C:\> Get-Command -Verb stop
Get Commands with start as a verb:
PS C:\> Get-Command -Verb Start
Get Help about Start-Process with examples:
PS C:\> Get-Help Start-Process -Examples | more
Start Notepad:
PS C:\> Start-Process Notepad.exe
Get Help about Stop-Process with examples:
PS C:\> Get-Help Stop-Process -Examples | more
Get processes with name containing notepad:
PS C:\> Get-Process -Name notepad
Stop a process by Id Number:
PS C:\> Stop-Process -Id <Id>
Get a list of HotFix installed:
PS C:\> Get-HotFix
Get Help containing "command":
PS C:\> Get-Help *command*
Get Help about Core Commands (more cmdlets):
PS C:\> Get-Help about_Core_Commands | more
cd \
dir
ls
ps
Get Help:
PS C:\> Get-Help
PS C:\> Get-Help *process
PS C:\> Get-Help *alias*
Download and install Help files on your computer:
PS C:\> Update-Help
List all alias you can use:
PS C:\> Get-Alias
Get Help for conceptual topics:
PS C:\> Get-Help Get-Help -Examples | more
Get Help for conceptual topics about alias:
PS C:\> Get-Help about_alias | more
Get Help about Get-Command
PS C:\> Get-Help Get-Command | more
Get all the commands:
PS C:\> Get-Command | more
Get all the commands (cmdlet only)
PS C:\> Get-Command -CommandType cmdlet | more
Get detailed Help about Get-Command:
PS C:\> Get-Help Get-Command -full | more
Get detailed Help about Get-Command (Parameter only):
PS C:\> Get-Help Get-Command -Parameter * | more
Get cmdlet with Name containing process:
PS C:\> Get-Command -CommandType cmdlet -Name *process*
Get cmdlet with Name containing service:
PS C:\> Get-Command -CommandType cmdlet -Name *service*
Measure Object (cmdlet only):
PS C:\> Get-Command -CommandType cmdlet | Measure-Object
Get all Processes:
PS C:\> Get-Process | more
Get all Services:
PS C:\> Get-Service | more
Get Commands with stop as a verb:
PS C:\> Get-Command -Verb stop
Get Commands with start as a verb:
PS C:\> Get-Command -Verb Start
Get Help about Start-Process with examples:
PS C:\> Get-Help Start-Process -Examples | more
Start Notepad:
PS C:\> Start-Process Notepad.exe
Get Help about Stop-Process with examples:
PS C:\> Get-Help Stop-Process -Examples | more
Get processes with name containing notepad:
PS C:\> Get-Process -Name notepad
Stop a process by Id Number:
PS C:\> Stop-Process -Id <Id>
Get a list of HotFix installed:
PS C:\> Get-HotFix
Get Help containing "command":
PS C:\> Get-Help *command*
Get Help about Core Commands (more cmdlets):
PS C:\> Get-Help about_Core_Commands | more
01 January 2020
Insecure Docker Registry I
Docker Registry is the most essential server when it comes to creating a docker environment. It holds all the images which are then pulled by other servers, and then containers get created. Unfortunately, most of the time, the Docker Registry remains unprotected, depending on how people have architected the docker environment.
Run nmap,
root@attackdefense:~# nmap -sV -n -p- 192.127.17.3
SERVICE/VERSION DETECTION:
-sV: Probe open ports to determine service/version info
HOST DISCOVERY:
-n/-R: Never do DNS resolution/Always resolve [default: sometimes]
PORT SPECIFICATION AND SCAN ORDER:
-p- to scan ports from 1 through 65535
Scan Results,
PORT STATE SERVICE VERSION
5000/tcp open http Docker Registry (API: 2.0)
Go to docker.com to learn Methods,
https://docs.docker.com/registry/spec/api/
Use curl to retrieve docker image name (repository),
Run nmap,
root@attackdefense:~# nmap -sV -n -p- 192.127.17.3
SERVICE/VERSION DETECTION:
-sV: Probe open ports to determine service/version info
HOST DISCOVERY:
-n/-R: Never do DNS resolution/Always resolve [default: sometimes]
PORT SPECIFICATION AND SCAN ORDER:
-p- to scan ports from 1 through 65535
Scan Results,
PORT STATE SERVICE VERSION
5000/tcp open http Docker Registry (API: 2.0)
Go to docker.com to learn Methods,
https://docs.docker.com/registry/spec/api/
| Method | Path | Entity | Description |
| GET | /v2/_catalog | Catalog | Retrieve a sorted, json list of repositories available in the registry. |
| GET | /v2/<name>/tags/list | Tags | Fetch the tags under the repository identified by name. |
Use curl to retrieve docker image name (repository),
curl http://192.127.17.3:5000/v2/_catalog
curl http://192.127.17.3:5000/v2/alpine/tags/list
Alternatively, using python for loop to automate fetching the repository,
Using requests.get and response.contect from requests library, https://realpython.com/python-requests/
Using json.loads from json library, https://realpython.com/python-json/

Source: attackdefense.com
Alternatively, using python for loop to automate fetching the repository,
Using requests.get and response.contect from requests library, https://realpython.com/python-requests/
Using json.loads from json library, https://realpython.com/python-json/

Source: attackdefense.com
Intro to ACCA F5 - Performance Management
PM Syllabus
- Costing techniques
- Decision-making techniques
- Budgeting and control
- Performance management
The Exam
Section A - 15 x 2 marks
Section B - 3 Scenarios x 5 x 2 marks
Section C - 2 x 20 marks.
Computer-based
- 3 hours 20 minutes
- Sections A and B - all objective test questions
- Extra 5 questions (2 marks each) do not count towards the overall mark.
- Section C - type out full answers using the built-in spreadsheet and word processor
- Pass mark - 50%
Credit to:
Subscribe to:
Comments (Atom)
Open Source Information Gathering using Windows Command Line Utilities
How to Find the Maximum Frame Size Packet needs to be fragmented but DF set, means that the frame is too large to be on the network and ne...

-
Planning and Operational variances Mix and Yield variances Advanced Idle Time variances Activity-Based...
-
Classification of MAC Address Entries Dynamic MAC address entries Static MAC address entries Blackhole MAC address entries Classifica...
-
Factors influencing selling price: costs competitors customers Cost-plus pricing 1. Full cost plus - Full cost includes a shared...